Quantum Safe
Description: “Project Name”
Business Statement
Quantum computing presents a growing threat to enterprise security, impacting everything from data encryption to core business operations across diverse industries. Customers are looking for guidance in starting their quantum safe journey.
- Quantum Computers can in principle, perform certain mathematical computations exponentially faster than a classical computer will.
- There will be a time when the power of quantum computing may crack public key cryptographic security protection.
- Your data and security is already at risk for quantum attacks.
- Cryptography impacts everything
Challenges
- Harvest now, decrypt later Hackers can collect data now for decryption when quantum computers are powerful enough.
- Replacing most of the public-key systems currently in use will take 5 to 15 years
- Lifetime of data means that sensitive data generated today that is not protected with quantum-safe algorithms is at risk now
With these considerations, many customers are asking the question: Ok, where do I start?
IBM’s leadership in the quantum space will guide customers in preparing for a post-quantum cryptography world.
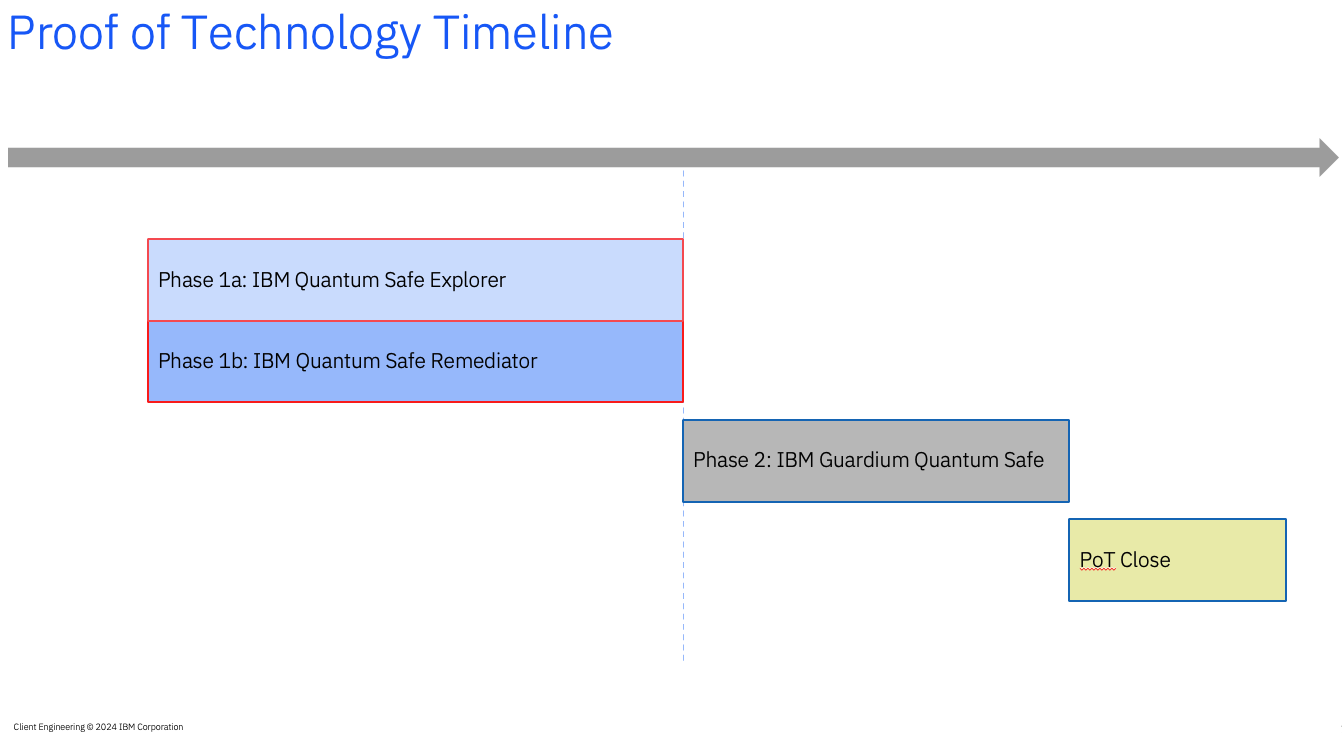
Proof of Technology - Scope
Goal Prove out the IBM Quantum Safe technologies. Demonstrate how they will help identify Cryptographic vulnerabilities and offer a plan of attack to protect their landscape from future Quantum Attacks.
- Quantum Safe Explorer Scan applications to discover cryptographic artifacts and vulnerabilities. Creates cryptographic inventory reports (CBOM).
- Quantum Safe Remediator
- Adaptive Proxy - protects communications between apps and end-user devices from quantum attacks. Positions proxy between your server & client’s
- Performance Test Harness - test quantum safe algorithms performance in environment before deploying to production.
| IBM Team Engaged |
|---|
| Client Engineering |
| Quantum Research |
| Customer Account Team |
| IBM Consulting |